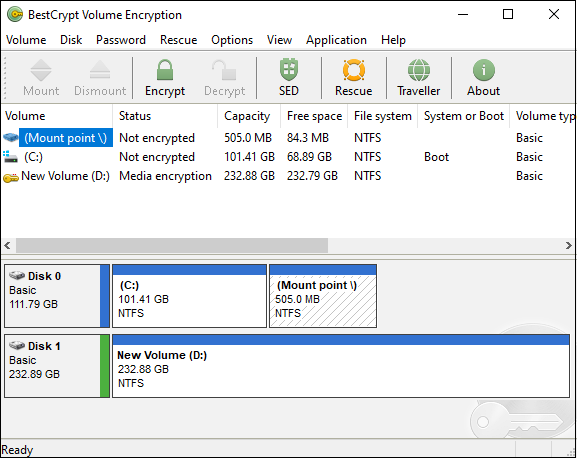
iStorage CloudAshur Hardware Security Module - Password Protected, Dust and Water Resistant, Portable, Military Grade Hardware Encryption - 5 Factor Authentication IS-EM-CA-256: Amazon.de: Computer & Zubehör

Encryption Done Right & Drive Configurations - The Crucial/Micron M500 Review (960GB, 480GB, 240GB, 120GB)

Kryptor FGPA is a Hardware Security Module that adds Complex Open-source Encryption - Electronics-Lab.com

Why Hardware Encryption is More Effective Than Software Encryption For Securing The Internet of Things - ELE Times