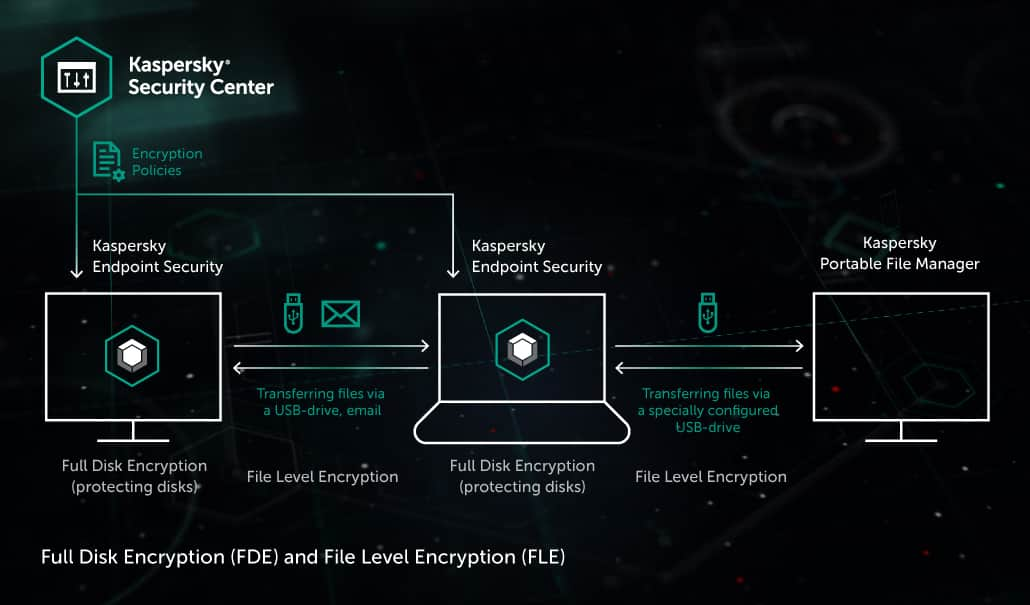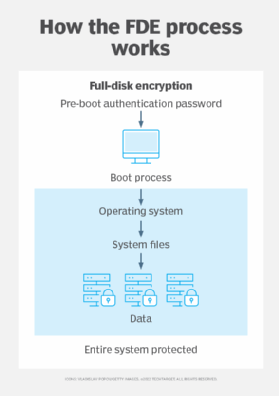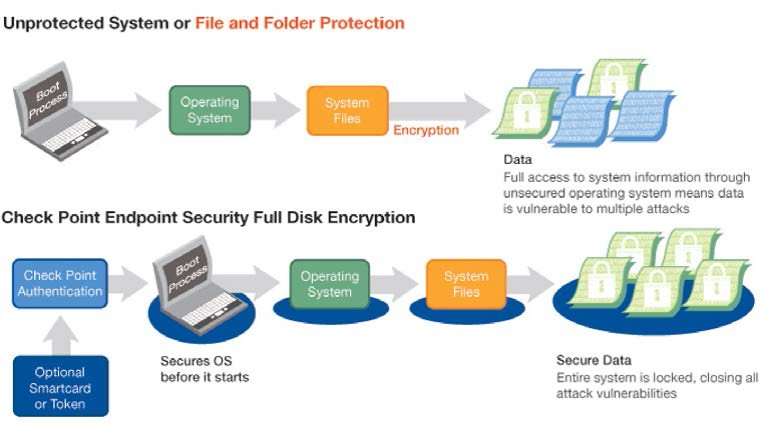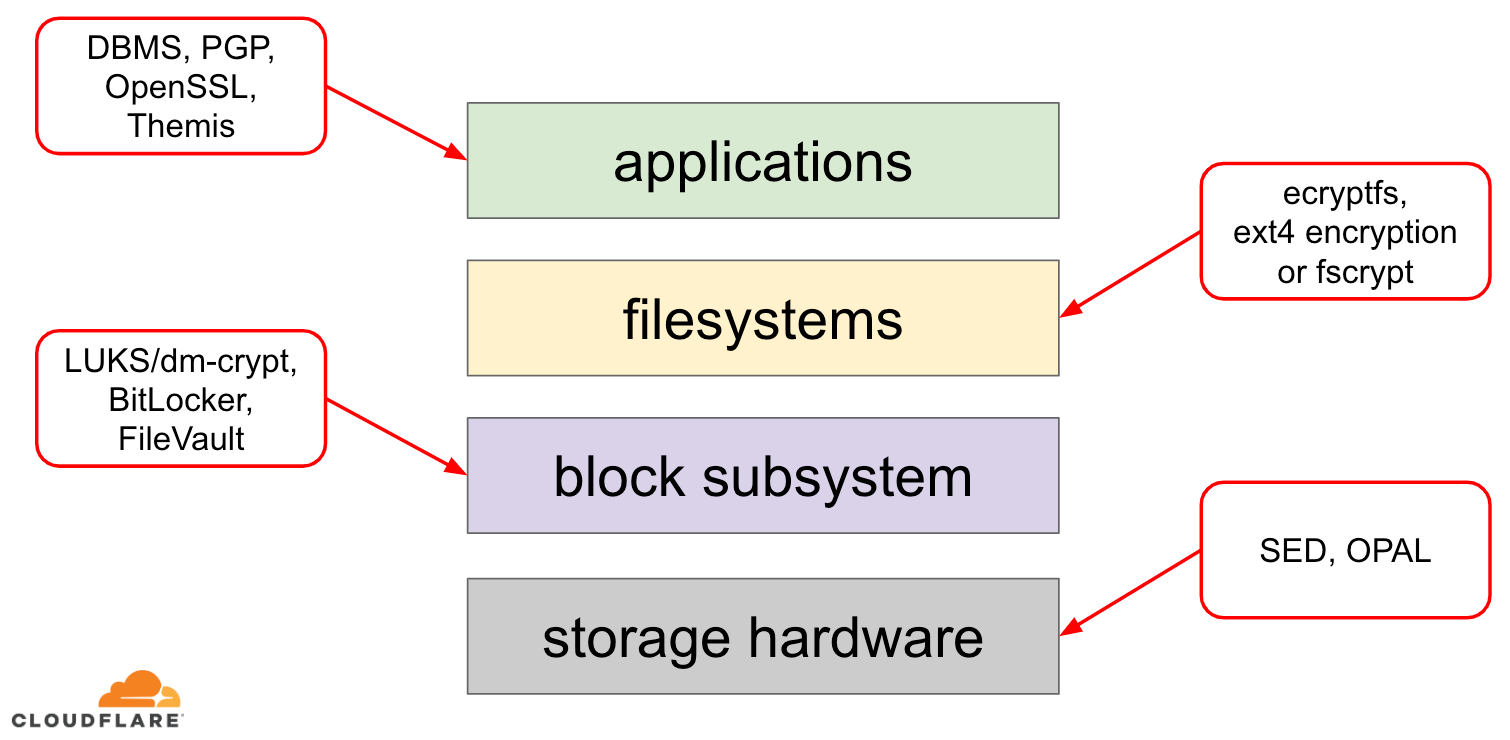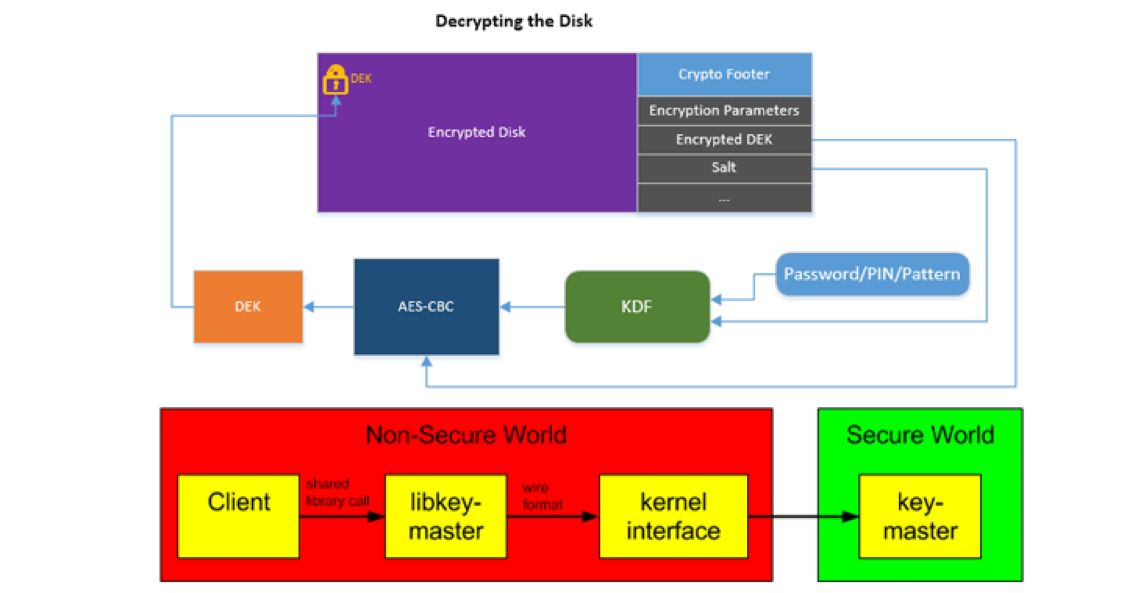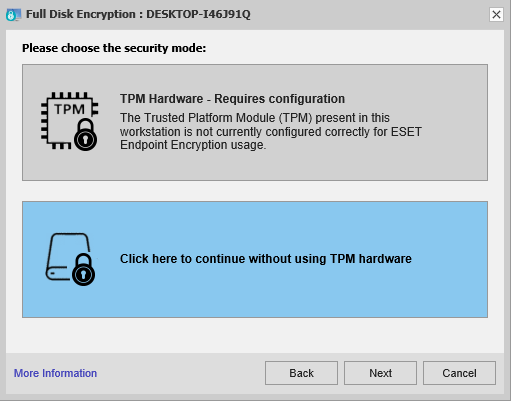
Full Disk Encrypt a client workstation using OPAL | ESET Endpoint Encryption Server | ESET Online Help

CISSP PRACTICE QUESTIONS – 20210316 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Istorage Datashur Pro 256-bit Usb Flash Drive Blue USB Flash Drives Hardware-based full disk encryption USB 3.0 iStorage datAshur 256-bit Flash Drive IS-FL-DA-256, USB, electronics, electronic Device, computer Hardware png | PNGWing

USB Flash Drives Hardware-based full disk encryption Computer hardware Hardware security module, Computer, computer, usb Flash Drive, electronic Device png | PNGWing

PDF) Software versus Hardware Full Disk Encryption – Comparison of Resistance to Attacks | Hasan Turaev - Academia.edu